Background and Motivation
In order to make waku-mix available for testing into the public waku network, it would be beneficial if we can implement libp2p-mix in javascript so that developers can start using mix and we can get better feedback of its performance and might help fine-tune and iterate on it. Existing apps using js-waku can also start using mix.
This document analyzes the implementation considerations for libp2p-mix in JavaScript, specifically focusing on browser-based applications and their integration with [js-waku](JavaScript Waku SDK | Waku Documentation"
It is possible some details have been missed which can be looked at and resolved during implementation.
Hoping that it would act as a reference for implementers(both js-mix and js-waku).
Overview
Currently, waku-mix integrates with request-response protocols such as lightpush and Store, which are primarily used by edge nodes."
Majority of apps are generally built using js-waku which would act as edge/light nodes.
The implementation consists of two main components:
- libp2p-mix implementation in javascript. Note that complete protocol implementation is not required.
- Changes in Waku
a. lightpush and store implementations to allow publishing using mix.
b. changes related to discovery
Implementing libp2p-mix in JavaScript
It would be good to refer [nim-mix](https://github.com/vacp2p/mix/tree/main-s2) implementation which is a reference implementation for the protocol.While we could implement the complete specification, initially js-waku only requires entry-side functionality—specifically packet sending logic and (https://cypherpunks.ca/~iang/pubs/Sphinx_Oakland09.pdf) reply processing.
There is no need to implement intermediate and exit node specific functionalities.
The mix implementation should be designed as a libp2p protocol and transport layer that integrates seamlessly with existing protocols."
The following components would be required to be implemented:
- Entry Connection similar to nim
- Send functionality which would be invoked while sending messages.
- Maintaining a mix node pool and using it to select peers for mix path.
- SURB handling at entry node when reply comes back.
- No need to implement fragmentation or any other extra functionality as it is expected for user’s of mix to fragment messages to the size that works with mix(current default is
4KB
Note that javascript already seem to have libraries that support sphinx packet encryption (such as sphinx-js or which would mean the cryptography would already be available to be integrated. This should make the implementation quicker and easier.
SURB specific logic
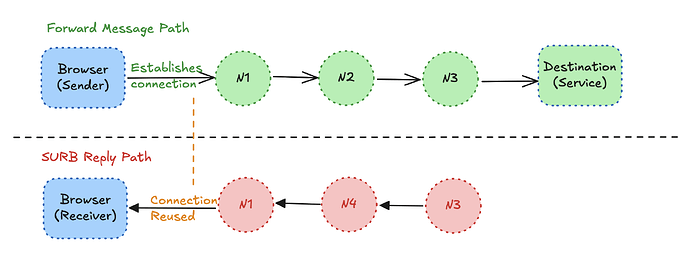
Browser environments have a fundamental limitation: external nodes cannot initiate connections to browsers (unless using WebRTC). This creates challenges for handling mix replies via [Single Use Reply Blocks](https://cypherpunks.ca/~iang/pubs/Sphinx_Oakland09.pdf)." In order to get around this limitation SURB should be generated as mentioned below in browser environments.When the forward message path is browser(sender) → N1 → N2 → N3 → destination, the SURB reply path should be constructed as N3 → N4 → N1 → browser. A brief illustration below of the same.
The key design principle is that the penultimate node in the reply path must match the first intermediate node from the forward path (N1 in this example). This ensures that N1 can reuse the existing connection established during the forward message transmission when relaying the reply back to the browser, rather than having to establish a new connection.
Updates in js-waku
js-waku functions solely as a sender node, utilizing lightpush and store protocols as a client/service-user. The lightpush and store send APIs should include an optional mixify flag to indicate when mix protocol should be used for packet transmission."
js-waku would require an initialization param which indicates whether mix is to be enabled or not. If mix is enabled the logic of maintaining a mix pool would be required to be implemented i.e as and when peers are discovered along with their ENR’s, they are required to be added to the mix-pool so that mix protocol layer can choose from the pool of nodes randomly while generating a path.
Logic to fragment messages before handing them over to mix layer.
@akshaya - Would love to get your feedback on the mix implementation section specifically.